Asset and Application Discovery
SANS critical security controls 1 and 2 define that an organization needs to have positive control of their assets
and applications in order to effectively develop a comprehensive security program.
You can't secure what you don't see.
Reclaim your organizational control.
Achieving a clear view of all devices connected to your network is paramount for identifying and managing vulnerabilities. With EITS’ Asset and Application Inventory solution:
- Gain a holistic view of network-attached devices.
- Proactively address and reduce risks from new devices and potential vulnerabilities.
But it doesn’t end there.
Application Inventory: Understand, Protect, Thrive.
- Assess every application operating within your network.
- Identify sensitive data sources and understand its flow – how it’s consumed, stored, and safeguarded.
Cloud Environment Inventory: Complete Oversight, Zero Blind Spots.
- Capture insights across various cloud platforms – SaaS, IaaS, and PaaS.
- With our advanced integration capabilities, we offer a genuine 100% inventory insight into all workloads your organization manages.
EITS ensures every corner of your network – from devices to cloud applications – is transparent and fortified.
When you choose EITS, we provide:
- Traffic & logs digested from multiple sources, which provide a more comprehensive analysis.
- In-depth and detailed data collected on all network devices and connected devices.
- Not limited to specific technology platforms, the discovery will find & analyze all devices with an IP address.
- Certified expert and in-depth analysis of what's collected.
- Ability to identify well-known vulnerabilities and detect common and weak clear text passwords in use across the network.
Managed Services Plans
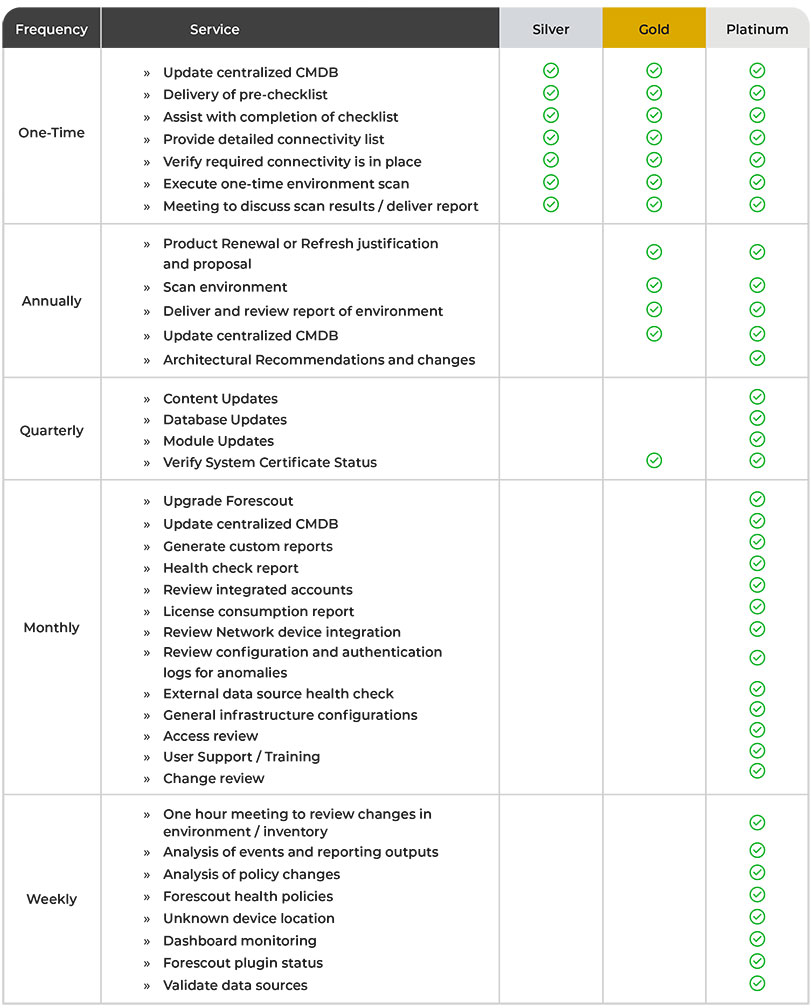
The EITS mission is “to understand each of our customers’ unique needs, guide them toward the right security investments, and provide the best possible professional services to defend their people and their data.”
Cyber Security Services
Resources
Contact
- (704) 900-8042
- 525 North Tryon St. Ste1600, Charlotte, NC 28202