Attack Simulation
Cyber-attacks can devastate your organization if you’re not prepared. Do you know how your company would respond to a real-world ransomware, supply chain, or other attacks?
Table of Contents
What is an Attack Simulation?
The EITS Attack Simulation takes some pretty advanced concepts from penetration testing, automates them, and makes it easy to deploy in any customer environment. What is interesting is it’s not quite a penetration test. So, let’s talk a little bit about what penetration testing is. A penetration test is where an ethical hacker tries to maneuver throughout the customer network, exploit various vulnerabilities, elevate access, and essentially steal all the information they can. This is not a full pen test because you cannot automate a pen test; it is just impossible. The EITS Attack Simulation does an excellent job of automating as many penetration test aspects as possible based on several real-world malicious actor campaigns.
Many different cyber gangs operate and through ransomware or other methods, cyber-attack organizations make or, more accurately, steal money. The common term in cyber lingo is APT (Advanced Persistent Threat). Another common acronym is TTP (Tactics, Techniques and Procedures). That is how the organization goes about attacking and maintaining control of the things they’ve hacked and how they stay hidden. It’s how they elevate access, steal, and exfiltrate your information. All of this is the TTP. Why does that matter? The EITS Attack Simulation takes all those decently well-known tactics and techniques and automates them so that you can run a simulated attack on your environment. You can simulate what these gangs would do if they were to get a foothold in your organization.
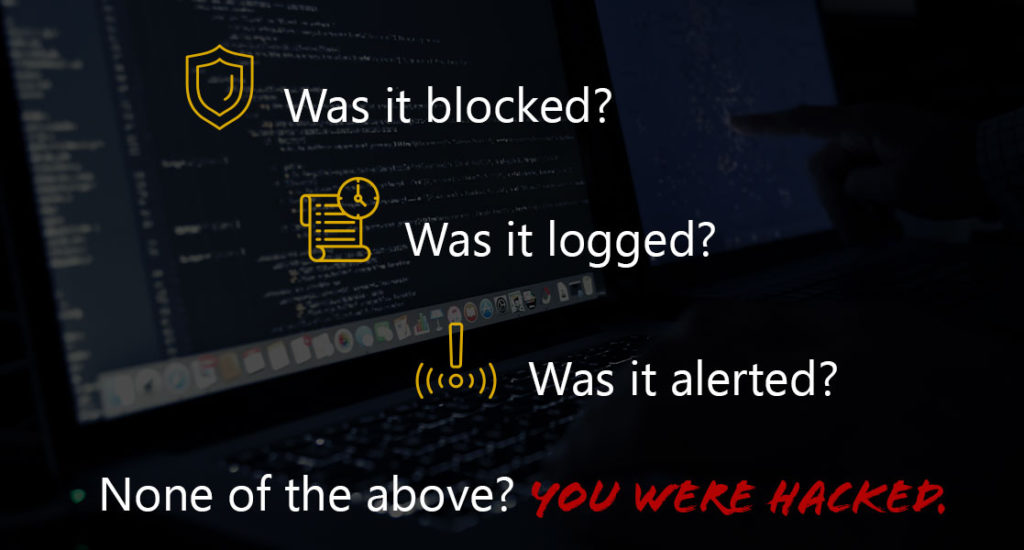
There Are Four Key Things That We Look For in These Attacks
- Was it blocked? Did the organization’s security stop it?
- Was it logged? Can the organization at least go back and see that the attack occurred?
- Was it alerted? Did they make it into the system? Did the organization detect it?
- None of the above and you are hacked.
Attack Simulations Provide Valuable, Actionable Data
Once we run the attack simulation through these scenarios, it generates a comprehensive and detailed report. That makes it quick and easy to determine how your organization did against the attack. After this report, the EITS staff can present and explain this information to your organization. With this information, we can determine how to fix or improve your security by coming up with recommendations on the preventative side so that you can start blocking these attacks as well as logging to ensure that the attacks are visible.
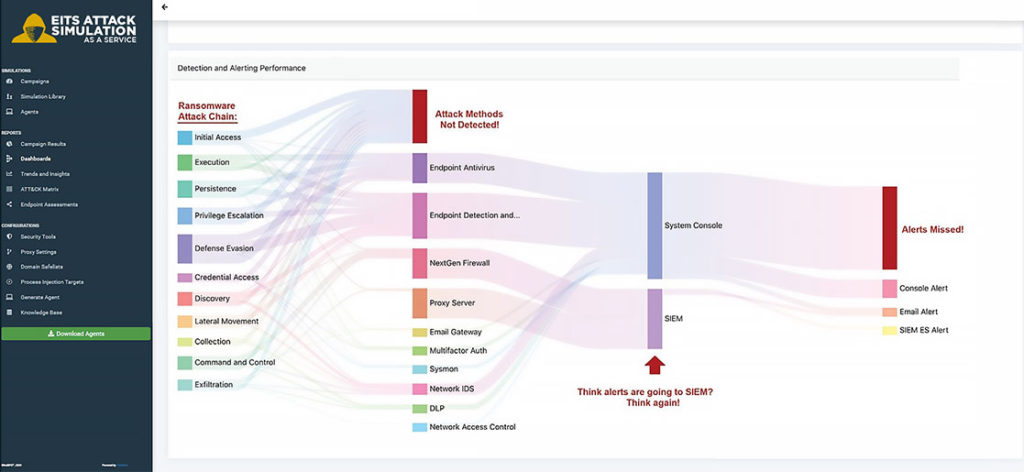
EITS Attack Simulation as a Service clearly visualizes gaps in your security configuration.
Agile Simulation Options to Fit Your Organization's Needs
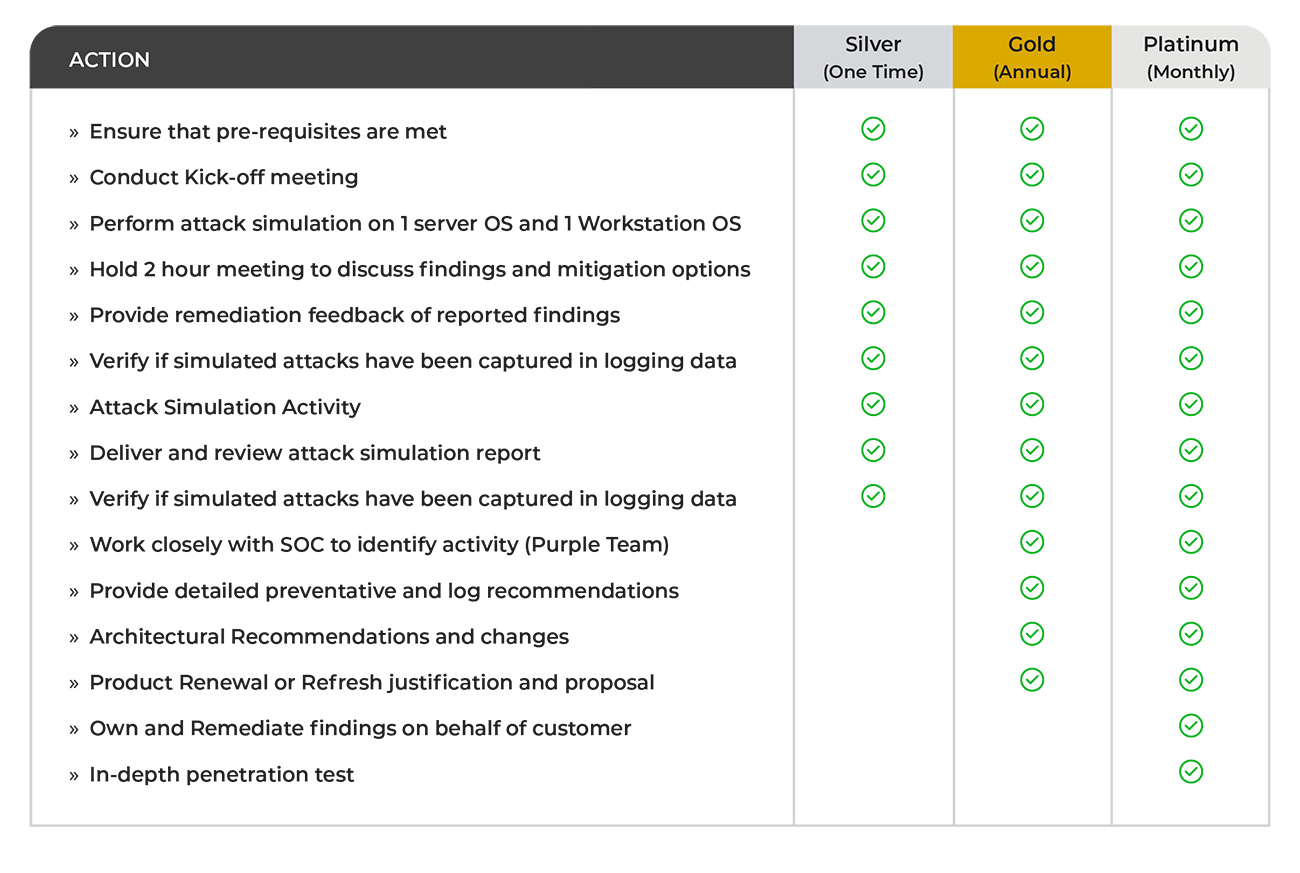
The EITS Attack Simulation as a service will be offered in three different tiers Silver, Gold, and Platinum. Let me elaborate on each one.
Silver would be a one-time assessment running the attack simulator and then a meeting afterward that would run through all the findings and give high-level recommendations based on the report generated.
The Gold tier would include the same as the silver but offer it as an annual service. We would also make much more detailed architectural recommendations to improve and help the organization’s security. This tier also includes purple teaming where EITS works with your SOC to ensure that they have visibility into all of the attacks.
The Platinum service includes all the above. Also, this is where EITS would have permission into the customer’s environment to make changes based on the reports and ownership to ensure that the customers environment is secure. It would also include a penetration test where one of our trained engineers would complete the attack simulation and then we would hand those results to one of our ethical hackers. They can use that information to provide further insight into other areas where the customer needs to improve their security.
Conclusion
The EITS Attack Simulation as a service shows how your organization responds to real-world security threats. To see the code used by malicious gangs and then have that bundled in a product that allows you to comprehend the data is a powerful tool. Don’t you want to know how your organization would fare against real-world attacks? From my point of view, the value of this service is that it enables us to accomplish a lot of valuable security in a concise amount of time. This service is the quickest way for us to assess your environment and give you real-world advice to enhance your security quickly and efficiently.
Attack Simulation
Stop your next cyber attack dead in its tracks.
Simulate Attacks | Test Controls | Level the Playing Field
Simulate Attacks | Test Controls | Level the Playing Field
The EITS mission is “to understand each of our customers’ unique needs, guide them toward the right security investments, and provide the best possible professional services to defend their people and their data.”
Cyber Security Services
Resources
Contact
- (704) 900-8042
- 525 North Tryon St. Ste1600, Charlotte, NC 28202