Table of Contents
CIS Controls Version 8
In May of 2021, the Center for Internet Security (CIS) released an updated version of their CIS Controls which guides security organizations in the kind of tasks required to become a mature, successful program. Historically these controls have been called the SANS Top 20, then the CIS 20 Critical Security Controls, and now the CIS 18 Controls. In this article, we want to point out the new changes to this framework and discuss how those changes help to further streamline the effort necessary to become a mature security organization.
In version 7 of the CIS Critical Security Controls, there were 20 control families, and they were divided into 3 categories: Basic, Foundational, and Organizational. The idea at the time was that if an organization followed the control families in numerical order, they would assemble their security program like building blocks stacked on top of one another and arrive at success.
CIS Controls Categories
The Basic category control families included Inventory, Vulnerability Management, Active Least Privilege Management, Configuration Baselining, and Log Monitoring. Successfully completing Inventory Management is a feat in itself that most organizations I assess have still not achieved and it has been a tenet of Security Operations for multiple decades. Vulnerability Management is easy to start but difficult to complete due to corporate politics. Most organizations perform regular scans of their environment but take little to no action to resolve them because it generates additional work for system administrators who already struggle to complete their primary duties within the work hours of the day.
The Reason for Version 8
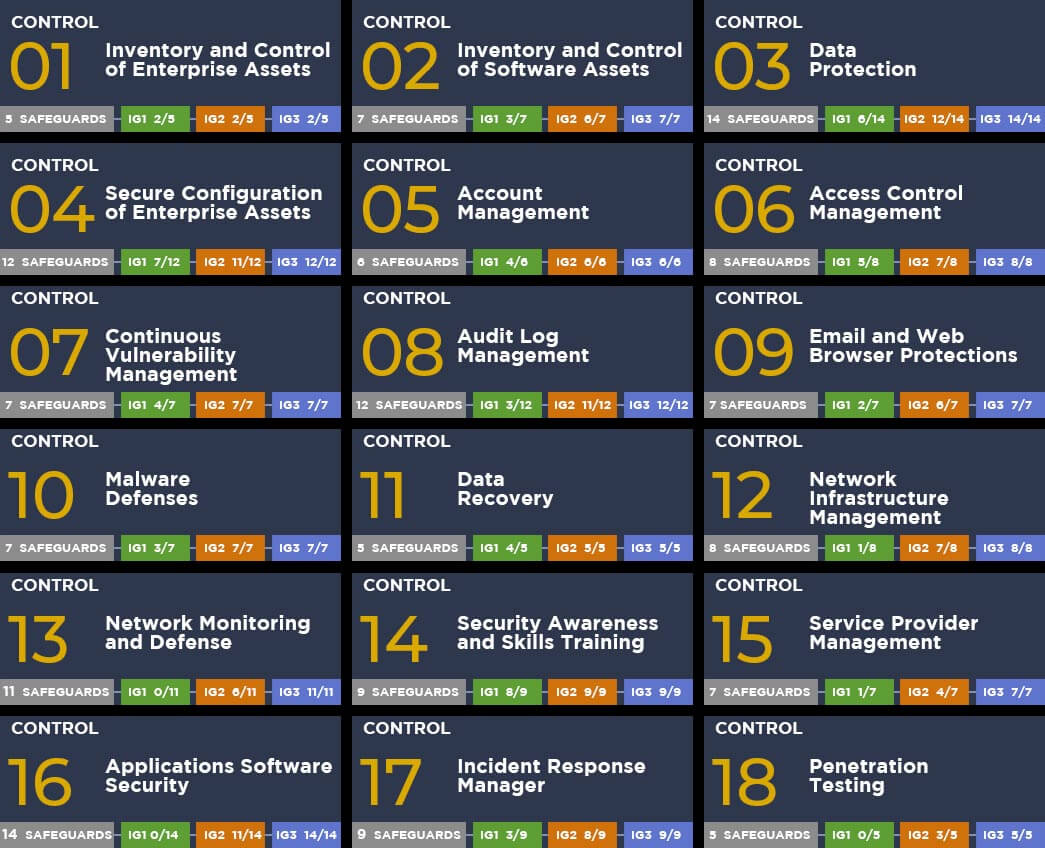
CIS Security Controls Version 8
Moving Forward
Conclusion
Cyber Security Services
Resources
Contact
- (704) 900-8042
- 525 North Tryon St. Ste1600, Charlotte, NC 28202